Would you bet a book on cupcake design would be a big seller? Or how about books titled “Erotic Poems” or “Awkward Family Photos?”
Thanks to emerging market trends, such off-beat books are big sellers – just not in traditional bookstores or big online sites such as Amazon. Publishers are increasingly turning to non-book retailers to sell their wares, according to an article in the New York Times. Lowe’s is selling books on cooking and home projects. Craft store Michaels is carrying the cupcake design book, and Urban Outfitters carries Awkward Family Photos.
The success of this new strategy lies in putting carefully selected physical books in front of people’s eyes, at full price. This may seem like a reversal of the trend toward e-books and online search capabilities, but in a way it reflects an emerging digital mentality – geographic space is becoming fragmented as an organizing concept. Heuristic thinking (a speculative exploration of possibilities) is in. As a colleague of mine commented, bookstores should have been offering free coffee – instead of coffee shops offering free books and newspapers.
So what is next? I’m trying to think of a book that will go over well at gas stations. Awkward Oil Changes? Don’t steal my idea, but you can purchase the following books to explore other options of selling books.
Monday, February 28, 2011
Sunday, February 27, 2011
Holographs join airline security staff
It sounds like a riddle: Meet staff who are always on duty, but never there.
As reported by The Telegraph, Manchester and London Luton became the first airports in the world earlier this year to use holographic staff. The new, all-digital staff are based on actual airline employees who work in security. Like their flesh-and-blood counterparts, the holograms remind passengers to have their boarding cards ready and give other security instructions to speed up security checks. The four, all of whom are attractive and wholesome-looking, are so life-like (see video) that reportedly some passengers are attempting to converse with them.
Technically, these are not real holograms. The holograms used by Manchester, for example, are life-like rear projections on a well-made surface. Nonetheless, they are sophisticated enough to give you the impression you are sharing space with a 3D person, according to the Singularity Hub. The Hub predicts a switch from life-like virtual projections to actual holograms and other 3D technologies that don't require as much space. In fact, telepresence with holographic display is one of the emerging technologies receiving increased attention this year, according to an article in TMCnet. It is drawing the attention of both artists and businesses, despite the challenges of high costs and elaborate setup.
So which do you prefer - a real security agent reminding you to have your documents ready, or a hologram?
Please consider the following sources for more knowledge about holographs;
As reported by The Telegraph, Manchester and London Luton became the first airports in the world earlier this year to use holographic staff. The new, all-digital staff are based on actual airline employees who work in security. Like their flesh-and-blood counterparts, the holograms remind passengers to have their boarding cards ready and give other security instructions to speed up security checks. The four, all of whom are attractive and wholesome-looking, are so life-like (see video) that reportedly some passengers are attempting to converse with them.
Technically, these are not real holograms. The holograms used by Manchester, for example, are life-like rear projections on a well-made surface. Nonetheless, they are sophisticated enough to give you the impression you are sharing space with a 3D person, according to the Singularity Hub. The Hub predicts a switch from life-like virtual projections to actual holograms and other 3D technologies that don't require as much space. In fact, telepresence with holographic display is one of the emerging technologies receiving increased attention this year, according to an article in TMCnet. It is drawing the attention of both artists and businesses, despite the challenges of high costs and elaborate setup.
So which do you prefer - a real security agent reminding you to have your documents ready, or a hologram?
Please consider the following sources for more knowledge about holographs;
Saturday, February 26, 2011
I'm guilty of mobile etiquette offenses - are you?
Do you use mobile devices while driving, talk on a mobile device loudly in public places, or use a mobile device while walking on the street? If so, you might want to watch your back!
According to a 2010 survey sponsored by Intel, the above three behavoirs are people's top pet peeves - the same as in 2009. Survey results also showed that three quarters of people believe mobile manners have gotten worse in the last year, and nine out of 10 people claim they have seen people misuse mobile technology. (Not surprisingly, only 20 percent of people claimed they misused it themselves).
Genevieve Bell, Intel Fellow and head of interaction and experience research, Intel Labs, said "Digital technology behavoirs are still embryonic, and it's important for Intel and the entire industry to maintain a dialogue about the way people use technology and our personal relationships with technology as they continue to help shape societal and cultural norms."
That's likely academic talk for, "We're not taking a stand." Personally, I wonder what the survey results say about our emerging culture. I can see the danger of talking on the phone and driving, but what's wrong with talking while walking on the street? I'm guilty, I admit it. And I don't mind when others do it - it's nice to see human interaction. Is there an unwritten code of silence in public places and streets that I'm missing? What's the difference if you're talking to a friend in person or on the cell? Does cell phone talk interfere with muzak? Share your view.
For more information on the subject please consider the following;
According to a 2010 survey sponsored by Intel, the above three behavoirs are people's top pet peeves - the same as in 2009. Survey results also showed that three quarters of people believe mobile manners have gotten worse in the last year, and nine out of 10 people claim they have seen people misuse mobile technology. (Not surprisingly, only 20 percent of people claimed they misused it themselves).
Genevieve Bell, Intel Fellow and head of interaction and experience research, Intel Labs, said "Digital technology behavoirs are still embryonic, and it's important for Intel and the entire industry to maintain a dialogue about the way people use technology and our personal relationships with technology as they continue to help shape societal and cultural norms."
That's likely academic talk for, "We're not taking a stand." Personally, I wonder what the survey results say about our emerging culture. I can see the danger of talking on the phone and driving, but what's wrong with talking while walking on the street? I'm guilty, I admit it. And I don't mind when others do it - it's nice to see human interaction. Is there an unwritten code of silence in public places and streets that I'm missing? What's the difference if you're talking to a friend in person or on the cell? Does cell phone talk interfere with muzak? Share your view.
For more information on the subject please consider the following;
Thursday, February 24, 2011
Blogging might cost your job - but should it?
I was talking to a K-12 teacher the other day about Natalie Munroe - the controversial Philadephia teacher who was suspended with pay after students discovered her blog on Feb. 8. In the blog, Munroe, a 30-year-old pregnant teacher at Central Bucks East High School, ranted about her students being "disobediant, disrespectful oafs" and "noisy, crazy, sloppy, lazy, LOAFERS." Talking about the rude kids in her honors class, she wrote,
"Something must be done about their disrespect and attitude problems. We should do away with the attitude of the students (and if we can't, we should do away with the students who have attitudes.) Better to have a pet - at least you know where you stand with a pet."
Munroe, who started her blog in 2009, was harshly criticized by Central Bucks Superintendent Robert Laws. No kids should have to be subjected to such a hostile environment, he said.
But the K-12 teacher I talked to thinks everyone should have the option to vent. "If you can't vent in a blog, where can you?" she asked. Munroe's lawyer likewise believes Munroe has a free-speech defence, and education blogger Alexander Russo asks, "Should teachers be limited to happy talk?"
Interestingly, Monroe's original blog, which did not use her full name and did not name her school or students, has been taken down. But Monroe has started a new blog, and this one makes no effort to be discreet: It's at www.nataliemunroe.com.
USA Today reports that while Monroe previously had nine followers, now she has 22. But people looking for outrageous comments - such as when Monroe wrote that teachers should be able to use "rat-like" and "dresses like a streetwalker" when writing report cards - might be disappointed. So far, Monroe has busied herself with defending and explaining her actions.
How are we going to communicate in a world of increasing smoke and mirrors? When should people keep their thoughts to themselves, and who's going to decide?
"Something must be done about their disrespect and attitude problems. We should do away with the attitude of the students (and if we can't, we should do away with the students who have attitudes.) Better to have a pet - at least you know where you stand with a pet."
Munroe, who started her blog in 2009, was harshly criticized by Central Bucks Superintendent Robert Laws. No kids should have to be subjected to such a hostile environment, he said.
But the K-12 teacher I talked to thinks everyone should have the option to vent. "If you can't vent in a blog, where can you?" she asked. Munroe's lawyer likewise believes Munroe has a free-speech defence, and education blogger Alexander Russo asks, "Should teachers be limited to happy talk?"
Interestingly, Monroe's original blog, which did not use her full name and did not name her school or students, has been taken down. But Monroe has started a new blog, and this one makes no effort to be discreet: It's at www.nataliemunroe.com.
USA Today reports that while Monroe previously had nine followers, now she has 22. But people looking for outrageous comments - such as when Monroe wrote that teachers should be able to use "rat-like" and "dresses like a streetwalker" when writing report cards - might be disappointed. So far, Monroe has busied herself with defending and explaining her actions.
How are we going to communicate in a world of increasing smoke and mirrors? When should people keep their thoughts to themselves, and who's going to decide?
Is the term 'False Positive' a critical digital literacy?
A false positive is another way of saying ‘error’. As applied to the field of digital programs, a false positive occurs when the program mistakenly flags an innocent file as being malicious or infected. This may seem harmless enough, but false positives can be a real nuisance and sometimes major problems if you are at a critical digital literacy disadvantage.
For example, from a digital computing perspective a) you waste even more time and resources in futile attempts to disinfect ‘infected’ files b) you waste productivity due to user down-time.
c) you may take e-mail offline, as a security precaution, thus causing a backlog and more lost productivity.
In short, digital false positives can be costly nuisances.
Unfortunately, the term is not confined. It also applies, for example, to anti-spam protection, where it refers to the misidentification of a legitimate e-mail message as spam. Since the undelivered e-mail may be a business critical message, this too could be very costly,
It can also apply to health and medical issues. For example, in a highly reported interview titled "Christina Applegate: MRI 'saved my life'" the following exchanged occured on the false positives in life threathening circumstances.
GUPTA: Most women, as you said, don’t know about MRIs with respect to screening for breast cancer.
APPLEGATE: Well it’s not talked about and I also think that you know, there’s also been a lot of talk that there’s all these false positives with MRIs but there are false positives with any kind of screening. Same with mammography – there is also a lot of false positives. They are not perfect science, unfortunately. But they’re learning more and more now that it’s, it’s an incredible way to screen for early detection.
GUPTA: One of the things I hear all the time as a doctor is that you doctors order too many tests – you’re ordering tests for everything. What do you say to people who say look we’re a culture of over-testing as it is? (Click here for the full interview)
What are your experiences with false positives? Do you agree its a critical digital literacy term to understand?
For some interesting literture on the subject, please consider purchasing the following;
For example, from a digital computing perspective a) you waste even more time and resources in futile attempts to disinfect ‘infected’ files b) you waste productivity due to user down-time.
c) you may take e-mail offline, as a security precaution, thus causing a backlog and more lost productivity.
In short, digital false positives can be costly nuisances.
Unfortunately, the term is not confined. It also applies, for example, to anti-spam protection, where it refers to the misidentification of a legitimate e-mail message as spam. Since the undelivered e-mail may be a business critical message, this too could be very costly,
It can also apply to health and medical issues. For example, in a highly reported interview titled "Christina Applegate: MRI 'saved my life'" the following exchanged occured on the false positives in life threathening circumstances.
GUPTA: Most women, as you said, don’t know about MRIs with respect to screening for breast cancer.
APPLEGATE: Well it’s not talked about and I also think that you know, there’s also been a lot of talk that there’s all these false positives with MRIs but there are false positives with any kind of screening. Same with mammography – there is also a lot of false positives. They are not perfect science, unfortunately. But they’re learning more and more now that it’s, it’s an incredible way to screen for early detection.
GUPTA: One of the things I hear all the time as a doctor is that you doctors order too many tests – you’re ordering tests for everything. What do you say to people who say look we’re a culture of over-testing as it is? (Click here for the full interview)
What are your experiences with false positives? Do you agree its a critical digital literacy term to understand?
For some interesting literture on the subject, please consider purchasing the following;
Wednesday, February 23, 2011
Pity the O
I am an 'O blood type.' That means, according to Peter D'Adamo, the author of Eat Right 4 Your Type, I am a universal blood donor, more prone to temper tantrums, and can eat more meat due to having an acidic stomach. The Os, as the most primitive of the four blood types - "the ancestral prototype was a canny, aggressive predator" - need to run through the forest when they get stressed, unlike 'As,' whose best bet is calming activities and meditation.
I have no idea if D'Adamo is on to something. His blood type-specific diets offer food for thought (i.e., Type As should avoid dairy products). So I would like to do a study of blood types and the use of social media. I know, blood types evolved through millions of years. Social media is what - a decade, two decades old?
But I want to know how an O differs from an A, B, or AB online. It can't be good for an O to be sitting at a computer. On other hand, the O feels compelled to lead. What are Os supposed to do with the world moving online? If you would like to participate or fund this important study, please let me know.
Please consider the following sources for more information;
I have no idea if D'Adamo is on to something. His blood type-specific diets offer food for thought (i.e., Type As should avoid dairy products). So I would like to do a study of blood types and the use of social media. I know, blood types evolved through millions of years. Social media is what - a decade, two decades old?
But I want to know how an O differs from an A, B, or AB online. It can't be good for an O to be sitting at a computer. On other hand, the O feels compelled to lead. What are Os supposed to do with the world moving online? If you would like to participate or fund this important study, please let me know.
Please consider the following sources for more information;
A provocateur (Malcolm Gladwell) keeps it up.
The Global Post has an interesting piece on Malcolm Gladwell, the best-selling author of "The Tipping Point," "Blink," and "Outliers." Gladwell insists social media sites such as Facebook and Twitter have not played a central role in the revolutions changing the landscape of the Middle East. In a Feb. 2 post in The New Yorker, Gladwell argued the "how" of a communcative act is not as important as the "why." High-risk social activism requires deep roots and strong ties, he argues - not exactly a characteristic of social meda. Revolutions have happened throughout history without Twitter.
But The Global Post argues that while Gladwell "deserves credit for reality-checking the hyperbole over the democratizing magic of social media," he doesn't address the question of why dictators (and regimes) find mass media so threatening. If a tree falls down in the middle of a forest and no one hears it, did it fall down?
Take the example of Indonesia in 1975, The Global Post explains. Entire villages in East Timor were getting slaughtered. Hoping for outside help, rebels put their faith in a precious piece of digital technology.
"Rebel leader Xanana Gusmao was desperate to alert the outside world to these crimes. But how? Surrounded by ocean and enemy territory, in the darkest years of the struggle, they relied on a Wagner 50-watt single sideband transceiver, which they hauled to mountain tops to transmit a staticky signal in hopes that supporters in Australia would be listening. The rebels rushed their broadcasts so that the enemy couldn’t track the signal and kill them. Complicating matters, only one man among them — “his nom de guerre was Hadomi,” Xanana told me — was strong enough to carry the massive transceiver battery. Eventually the Indonesians killed Hadomi, and the rebels were silenced."
Would more people in East Timor have survived if they managed to transmit a bit longer? Would Australians have rushed to help if only the rebels had posted photos on Facebook? History doesn't allow reruns, at least at this point.
But the story points to the complexity of unraveling social media's role. Gladwell, a sociologist, tends toward deterministic (inevitable) theories. "How" is put in its box as neatly as "why," without considering the morphings that perhaps do not repeat history and cannot be easily explained. Has the force of everyday oppression and the glimmers of escape through social media played out in the past? Is there something fundamentally new about humans and the digital environment, or does social media just represent a faster or different way to communicate, as Gladwell argues. What do you think?
But The Global Post argues that while Gladwell "deserves credit for reality-checking the hyperbole over the democratizing magic of social media," he doesn't address the question of why dictators (and regimes) find mass media so threatening. If a tree falls down in the middle of a forest and no one hears it, did it fall down?
Take the example of Indonesia in 1975, The Global Post explains. Entire villages in East Timor were getting slaughtered. Hoping for outside help, rebels put their faith in a precious piece of digital technology.
"Rebel leader Xanana Gusmao was desperate to alert the outside world to these crimes. But how? Surrounded by ocean and enemy territory, in the darkest years of the struggle, they relied on a Wagner 50-watt single sideband transceiver, which they hauled to mountain tops to transmit a staticky signal in hopes that supporters in Australia would be listening. The rebels rushed their broadcasts so that the enemy couldn’t track the signal and kill them. Complicating matters, only one man among them — “his nom de guerre was Hadomi,” Xanana told me — was strong enough to carry the massive transceiver battery. Eventually the Indonesians killed Hadomi, and the rebels were silenced."
Would more people in East Timor have survived if they managed to transmit a bit longer? Would Australians have rushed to help if only the rebels had posted photos on Facebook? History doesn't allow reruns, at least at this point.
But the story points to the complexity of unraveling social media's role. Gladwell, a sociologist, tends toward deterministic (inevitable) theories. "How" is put in its box as neatly as "why," without considering the morphings that perhaps do not repeat history and cannot be easily explained. Has the force of everyday oppression and the glimmers of escape through social media played out in the past? Is there something fundamentally new about humans and the digital environment, or does social media just represent a faster or different way to communicate, as Gladwell argues. What do you think?
Monday, February 21, 2011
Bloggers gone wild...
A New York Times article today describes a dramatic drop in blogging among the young. By "young," the NYT is referring to 12 to 17 year olds. Fourteen percent have blogs - a decline of half from 2006, when about 30 percent of that age group who used the Internet had blogs.
At the same time, older age groups are blogging more. As the NYT describes,
"Among 34-to-45-year-olds who use the Internet, the percentage who blog increased six points, to 16 percent, in 2010 from two years earlier... Blogging by 46-to-55-year-olds increased five percentage points, to 11 percent, while blogging among 65-to-73-year-olds rose two percentage points, to 8 percent."
The NYT concludes that the young, discouraged by lack of readers, are shifting to Facebook, Twitter, and Tumblr., which is mainly images and doesn't involve as much writing. By contrast, "serious" bloggers are into more serious analysis and using several mediums to generate traffic.
I had no clue so many teens were blogging, or that so many people in general were blogging. Maybe people like to write more than you'd guess, given educators' deep concern over reading test scores. Then again, statistics are tricky. What do you think?
At the same time, older age groups are blogging more. As the NYT describes,
"Among 34-to-45-year-olds who use the Internet, the percentage who blog increased six points, to 16 percent, in 2010 from two years earlier... Blogging by 46-to-55-year-olds increased five percentage points, to 11 percent, while blogging among 65-to-73-year-olds rose two percentage points, to 8 percent."
The NYT concludes that the young, discouraged by lack of readers, are shifting to Facebook, Twitter, and Tumblr., which is mainly images and doesn't involve as much writing. By contrast, "serious" bloggers are into more serious analysis and using several mediums to generate traffic.
I had no clue so many teens were blogging, or that so many people in general were blogging. Maybe people like to write more than you'd guess, given educators' deep concern over reading test scores. Then again, statistics are tricky. What do you think?
Saturday, February 19, 2011
IBM’s Watson wins on Jeopardy!
After the famous “thinking” computer Watson beat its human contestants on Jeopardy this week, NPR Weekend Edition Saturday took a stab at how the Human Being is still unique: The Human Being is the only creature/machine that can laugh at, “Why did the chicken cross the road?”
Really? I always had trouble with that joke. Should I be worried?
Read about Watson’s innards - "deep NLP with machine learning, a voting algorithm, a method of interpreting the questions and assessing them by formulating parallel hypotheses, and Hadoop and UIMA for preprocessing, as well as the usual search, fuzzy matching software and of course an in-memory caching system to save time in retrieval" - at PCWorld.
Really? I always had trouble with that joke. Should I be worried?
Read about Watson’s innards - "deep NLP with machine learning, a voting algorithm, a method of interpreting the questions and assessing them by formulating parallel hypotheses, and Hadoop and UIMA for preprocessing, as well as the usual search, fuzzy matching software and of course an in-memory caching system to save time in retrieval" - at PCWorld.
I'd rather eat a plate of spiders...
The New York Times Magazine today carried a story about mental athletes, "or M.A.'s for short." These mental athletes - who were competing in the U.S.A. Memory Championship - can memorize thousands of random digits in under an hour. According to the article, they use techniques handed down from the ancient Greeks (who were not living in an era when more than a million books are published a year). This includes using spatial thinking and visual images - such as creating a unique image for every number from 0 to 999,999,999, or creating a memory palace for a series of cards.
Does this have anything to do with critical thinking? Personally I dislike memorizing many things, including passwords - a personal, hugely annoying roadblock in moving toward critical digital literacy. There seem to be a ton of sites on critical thinking, but little consensus on the issue. After a quick search, I tenatively decided the answer is no, you don't need a good memory - or any memory? - to be a critical thinker. I settled on the overview provided by Asking the Right Questions - A Guide to Critical Thinking, 9th edition. The author's blog might be more interesting, if you like contemplating this kind of stuff.
For additional information regarding critical thinking please consider the following sources;
Does this have anything to do with critical thinking? Personally I dislike memorizing many things, including passwords - a personal, hugely annoying roadblock in moving toward critical digital literacy. There seem to be a ton of sites on critical thinking, but little consensus on the issue. After a quick search, I tenatively decided the answer is no, you don't need a good memory - or any memory? - to be a critical thinker. I settled on the overview provided by Asking the Right Questions - A Guide to Critical Thinking, 9th edition. The author's blog might be more interesting, if you like contemplating this kind of stuff.
For additional information regarding critical thinking please consider the following sources;
Friday, February 18, 2011
Do you know what your megabit-per-second download speed is?
A Commerce Department survey provides some initial evidence that yes, a digital divide exists – thanks in part to murky business practices.
The information, compiled in a national broadband map, shows which populations have access to high-speed internet.
In DC, only 12 percent of homes can get broadband speeds as high as 25 megabits per second – compared to 98 percent of homes in Montgomery County and 99 percent of homes in Fairfax and Arlington Counties.
The survey doesn’t include pricing or real (vs company advertised) speed information. Still, it provides new information that documents the digital divide, notes The Washington Post in an article today.
The information, compiled in a national broadband map, shows which populations have access to high-speed internet.
In DC, only 12 percent of homes can get broadband speeds as high as 25 megabits per second – compared to 98 percent of homes in Montgomery County and 99 percent of homes in Fairfax and Arlington Counties.
The survey doesn’t include pricing or real (vs company advertised) speed information. Still, it provides new information that documents the digital divide, notes The Washington Post in an article today.
Thursday, February 17, 2011
Who is really an “expert”?
Science is increasingly taking place in institutions such as universities. But the institutions are losing the trust of the public, argues philosopher Naomi Scheman. So while expertise is being institutionalized, “experts” are less trustworthy.
So who is really an expert?
We all need to know if the water is safe to drink. But would you trust an institution to tell you the water is safe to drink? “Unverifiable expertise,” much like power and privilege over others, is an increasing problem, Scheman says. There is truth and reality – but truth and reality cannot be claimed by just one group claiming to speak for everyone.
Expertise needs to be on the side of the public. Equally important, the public needs to have a say in the questions “experts” ask. We can best understand objectivity and truth as public goods, Scheman says. After all, the notion of rational individual thought was itself the result of public, engaged epistemology – how do we know what we know.
In summary, “expertise” cannot exit without our critical thinking and input.
Read a 2010 article by Scheman at: If you care about truth, fight for justice
Want to delve further? Check out: Meeting the Universe Halfway: Quantum Physics and the Entanglement of Matter and Meaning (2007).
So who is really an expert?
We all need to know if the water is safe to drink. But would you trust an institution to tell you the water is safe to drink? “Unverifiable expertise,” much like power and privilege over others, is an increasing problem, Scheman says. There is truth and reality – but truth and reality cannot be claimed by just one group claiming to speak for everyone.
Expertise needs to be on the side of the public. Equally important, the public needs to have a say in the questions “experts” ask. We can best understand objectivity and truth as public goods, Scheman says. After all, the notion of rational individual thought was itself the result of public, engaged epistemology – how do we know what we know.
In summary, “expertise” cannot exit without our critical thinking and input.
Read a 2010 article by Scheman at: If you care about truth, fight for justice
Want to delve further? Check out: Meeting the Universe Halfway: Quantum Physics and the Entanglement of Matter and Meaning (2007).
Cyber..Virtual..Digital-Crime
Diffusion and Effects of Cyber-Crime in Developing Economies : NIR KSHETRI
ABSTRACT: Cyber-crime’s footprints across the developing world are getting bigger. The aim of this article is to examine the structure of cyber-crimes in developing economies. Its central idea is that economic and institutional factors facing cyber-criminals and potential victims in the developing world are different from those in the developed world. In economies characterised by low internet penetration rates and few resources devoted to fighting cyber-crimes, formal institutions related to such crimes tend to be thin and dysfunctional. A cyber-criminal is less likely to be stigmatised in such economies. Moreover, organisations’ and individuals’ technological and behavioural defence mechanisms are likely to be weaker. Many people in developing economies are also attracted into cyber-crime because of high unemployment and low wages.
------------------------------------------------------------------------------------------------
After reviewing the aforementioned report and considering the latest media reporting about cyber crimes, I'm reminded to continue to stress the importance of critical digital literacy. With over 100 books at my disposal that deals with information security, communication systems design, criminal investigations, penetration testing (hacking), and computer crime investigation (digital forensics) I can confirm that the aforementioned report has valid and accurate information. Several for my friends are working in digital forensics at the local/state/federal levels in law enforcement have collaborated about similar incidents reported in the material. The books below are good because they collectively covers what REALLY happens out in the field during a digital computer crime investigation (including entire chapters on what to bring, how to plan, who to work with, etc). Also included are entire chapters dedicated to various tools and step by step instructions on how to use them. Some of the authors are still outstanding writers, speakers and investigator in the digital forensics world, working with corporations, government agencies, law enforcement, and global military. I recommend the aforementioned report and the following books for both novices and those with experience.
ABSTRACT: Cyber-crime’s footprints across the developing world are getting bigger. The aim of this article is to examine the structure of cyber-crimes in developing economies. Its central idea is that economic and institutional factors facing cyber-criminals and potential victims in the developing world are different from those in the developed world. In economies characterised by low internet penetration rates and few resources devoted to fighting cyber-crimes, formal institutions related to such crimes tend to be thin and dysfunctional. A cyber-criminal is less likely to be stigmatised in such economies. Moreover, organisations’ and individuals’ technological and behavioural defence mechanisms are likely to be weaker. Many people in developing economies are also attracted into cyber-crime because of high unemployment and low wages.
------------------------------------------------------------------------------------------------
After reviewing the aforementioned report and considering the latest media reporting about cyber crimes, I'm reminded to continue to stress the importance of critical digital literacy. With over 100 books at my disposal that deals with information security, communication systems design, criminal investigations, penetration testing (hacking), and computer crime investigation (digital forensics) I can confirm that the aforementioned report has valid and accurate information. Several for my friends are working in digital forensics at the local/state/federal levels in law enforcement have collaborated about similar incidents reported in the material. The books below are good because they collectively covers what REALLY happens out in the field during a digital computer crime investigation (including entire chapters on what to bring, how to plan, who to work with, etc). Also included are entire chapters dedicated to various tools and step by step instructions on how to use them. Some of the authors are still outstanding writers, speakers and investigator in the digital forensics world, working with corporations, government agencies, law enforcement, and global military. I recommend the aforementioned report and the following books for both novices and those with experience.
Tuesday, February 15, 2011
Second Chance Act Technology Careers Training Demonstration Projects for Incarcerated Adults and Juveniles
Review the following information to get a sense of how much the demand for digital literacy has grown. Basically, when enforcement recognise the potential of technology knowledge to reduce crime and violent activitity, its a indication to individuals to seek critical digital literacy.
1. What are the purposes and expectations for this program?
To provide technology career training to persons confined in state prisons, local jails, and juvenile residential facilities.
2. What is the goal of the program?
To increase the post-release employability of offenders in related technology-based jobs and career fields.
3. What is the objective of the program?
To establish and provide technology career training programs to train incarcerated adults and juveniles during the 3-year period before release from a prison, jail, or juvenile facility.
4. What are the eligibility requirements under this program?
Applicants are limited to states, units of local government, territories, and federally recognized Indian tribes (as determined by the Secretary of the Interior).
5. Are there specific requirements that must be adhered to for the program?
To receive an award under this announcement, applicants must adhere to the following deliverables and mandatory requirements:
All applications are due by 11:59 p.m. eastern time on March 3, 2011.
9. When will applicants be notified if they are successful?
Awards should be announced before the end of the federal fiscal year on September 30, 2011.
10. How quickly after receiving notice will a grant recipient be expected to launch their program?
Actual funding access to award recipients is dependent on final budget clearance and adherence to Special Condition requirements. However, award recipients should anticipate begin providing services no later than 90 days after receiving notice.
Target Population
12. What is the target population for this program?
The target population should be incarcerated adults and juveniles within a 3-year period before release from a prison, jail, or juvenile facility. The target population for the initiative must be a specific subset of the population of individuals convicted as an adult or adjudicated as a juvenile, and incarcerated in a state, local, or tribal prison; jail or a juvenile detention/correctional facility; juvenile camp; juvenile community-based program; or a juvenile residential facility. For federally recognized Indian tribes, the individuals may be housed in a tribal, state, regional, county, or local jail facility pursuant to state or tribal law.
Applicants must provide justification for selecting the target population and provide supporting documentation for their decision.
15. May funded programs target specific people who are overrepresented in the criminal justice system?
As a condition for receiving funding, recipients must comply with applicable federal civil rights laws, including Title VI of the Civil Rights Act of 1964. Federal law prohibits a recipient of funding from discriminating in the delivery of services or benefits on the basis of race, color, national origin, sex, religion, or disability. While applicants may design their program to maximize participation by any population overrepresented in the criminal justice system, they may not accept or reject otherwise eligible participants on the basis of their race.
Program-Specific Requirements
It is not required or mandatory that applicants collaborate with technology industry-related organizations. However, priority consideration will be given to applications that partner with technology industry-related organizations and other entities that can provide resources or expertise to the project. Applicants should demonstrate a high degree of collaboration with workforce employers, and provide documentation demonstrating partnerships, agreements, or memoranda of understanding with relevant employers in the technology areas to which program participants are likely to return.
In addition, priority consideration will be given to applicants that partner with technology industry-related organizations and other entities (including local and small businesses) willing to hire and support high-risk offenders through the learning and job training process.
20. Are applicants required to restrict access to any technology tools or resources?
Yes. Applicants must restrict access to the internet by incarcerated persons, as appropriate, to ensure public safety.
23. What are the performance measures for this program?
The performance measures will require the tracking of key data points. An example would be the Performance Measure, “Percentage of trainees who successfully completed the in-person training program,” which will require the grantee to provide the following data points:
• Number of individuals who completed the training
• Number of individuals who attended each training
A complete list of the Performance Measures can be found on pages 7-9 of the solicitation.
24. What software or tools should grantees use to track performance measures? Are these tools provided by BJA?
25. How long will grantees need to track client’s performance measure data listed in solicitation? Beyond the funding period?
Recipients may be required to track clients beyond the end of the period for which they receive federal funding. BJA will provide further guidance and assistance to recipients on data collection.
Budget/Allowable Uses
No.
28. Can grant funds be used to subsidize employers or fund transitional employment programs?
Yes. Award funds may be used for post-release services for a maximum 6-month period that provides support for program participants engaged in paths to technology-based careers, including voucher/stipend support.
29. Does the entire award amount need to be used within the award period?
No. No‐cost extensions will be available to grantees, subject to the approval of BJA. If all award funds are not used (spent) within the award period and completion of the project, the funds will be de-obligated.
30. Are there any limitations on how award funds can be used for employee compensation?
With respect to any award of more than $250,000 made under this solicitation, federal funds may not be used to pay total cash compensation (salary plus bonuses) to any employee of the award recipient at a rate that exceeds 110% of the maximum annual salary payable to a member of the Federal Government’s Senior Executive Service (SES) at an agency with a Certified SES Performance Appraisal System for that year.
A recipient may compensate an employee at a higher rate, provided the amount in excess of this compensation limitation is paid with non-federal funds. The limitation on compensation rates allowable under an award may be waived on an individual basis at the discretion of the Assistant Attorney General (AAG) for the Office of Justice Programs (OJP).
31. Is there a match requirement for this program?
This solicitation does not require a match.
32. Some federal grants require applicants to set aside funds for travel to mandatory grantee meetings. Should mentoring grant applicants budget for any particular training or technical assistance?
Applicants must budget funding to travel to U.S. Department of Justice-sponsored grant meetings. Applicants should estimate the costs of travel and accommodations for three staff to attend two meetings in Washington, D.C.
Collaboration
33. Can a collaboration of entities apply as one applicant?
Yes. However, only one state, unit of local government, territory, or federally recognized Indian tribe, must be designated as the “official” applicant. Priority consideration will be given to applications that demonstrate a high degree of collaboration with workforce employers, and provide documentation demonstrating partnerships, agreements, or memoranda of understanding with relevant employers in the technology areas to which program participants are likely to return.
Technical Application Questions
34. Does the budget narrative count against the 15 page limit?
No.
35. Are there any priority considerations that will be given when evaluating applications for awards?
Priority consideration will be given to applications that:
All applications will be peer reviewed based on the solicitation requirements. The Directors of BJA and Office of Juvenile Justice and Delinquency Prevention (OJJDP) will then make award recommendations to the AAG for OJP, who will make final determinations.
37. If the state is not applying, can more than one local jurisdiction apply in that state?
Yes, it is possible for several cities, counties, and the state to apply since all are independent jurisdictions.
38. Is there a percentage breakdown for allocation to state versus local government?
No. BJA is cognizant of the need for geographical distribution as well as some level of equity among states, locals, and tribes.
39. How will submissions from multiple jurisdictions in the same state be viewed? How would it reflect on a state if multiple agencies applied from that state?
Submissions from multiple jurisdictions in the same state will be viewed on the individual merit of each application that meets the solicitation requirements.
Other
41. Will there be future opportunities to apply for funding under this program?
All future BJA funding opportunities will be based on Congressional approved appropriations.
42. Can grant funds be used to enhance existing reentry programs, or are funds limited to new programs?
Federal funds cannot be used to supplant existing services. Federal funds provided under the Second Chance Act are meant to be one of the sources of program funding. They may not to be used to replace other funding sources.
43. Is there someone specific to contact with questions about the process or program?
For technical assistance with submitting the application, contact the Grants.gov Customer Support Hotline at 800–518–4726 or via e-mail to support@grants.gov. The Grants.gov Support Hotline hours of operation are 24 hours, 7 days a week, except federal holidays.
For assistance with any other requirement of this solicitation, contact the BJA Justice Information Center at 1–877–927–5657. The BJA Justice Information Center hours of operation are 8:30 a.m. to 5:00 p.m. eastern time, Monday through Friday, and 8:30 a.m. to 8:00 p.m. eastern time on the solicitation close date.
1. What are the purposes and expectations for this program?
To provide technology career training to persons confined in state prisons, local jails, and juvenile residential facilities.
2. What is the goal of the program?
To increase the post-release employability of offenders in related technology-based jobs and career fields.
3. What is the objective of the program?
To establish and provide technology career training programs to train incarcerated adults and juveniles during the 3-year period before release from a prison, jail, or juvenile facility.
4. What are the eligibility requirements under this program?
Applicants are limited to states, units of local government, territories, and federally recognized Indian tribes (as determined by the Secretary of the Interior).
5. Are there specific requirements that must be adhered to for the program?
To receive an award under this announcement, applicants must adhere to the following deliverables and mandatory requirements:
- Demonstrate an understanding of the value of technological training for offenders reentering the community from prisons, jails, and juvenile facilities.
- Specify and include a process or plan for identifying, referring, and assessing potential participants into the training program.
- Include a curriculum that helps participants acquire and develop skills needed to build potentially successful careers in technology-related fields. The training curriculum must identify necessary skills and competencies, provide real-world work experience, teach transferable job skills and soft skills to help prepare for post-release reentry and employment, and provide resources to support training in technology areas.
- Provide incarcerated adults and juveniles with paths to career opportunities in technology-based fields by utilizing a variety of learning strategies to assist with performing work-related activities.
- Incorporate the following activities: address skills and competencies demanded by the targeted technology career; support participants’ advancement along a defined career pathway; and, where applicable, result in a recognized certificate, degree, or license that indicates a level of mastery and competence in a given technology based on the type of training completed.
- Highlight, when at all possible, evidence-based programs or practices.
- Restrict access to the Internet by incarcerated persons, as appropriate, to ensure public safety.
- Submit to BJA a report no later than 90 days after the last day of the final fiscal year of the award that describes and assesses the uses of award funds during the preceding fiscal year.
All applications are due by 11:59 p.m. eastern time on March 3, 2011.
7. What is the potential project length for an award?
As required by the statute, any awards made under this program will be made for a period of up to 12 months.8. What are the award amounts for projects?
Contingent upon the availability of funds, awards of up to $750,000 each may be made. Pending the outcome of the FY 2011 appropriations process anticipated in March 2011, BJA may make as few as no awards and as many as five awards this fiscal year under this program. All awards are subject to the availability of appropriated funds and any modifications or additional requirements that may be imposed by law.9. When will applicants be notified if they are successful?
Awards should be announced before the end of the federal fiscal year on September 30, 2011.
10. How quickly after receiving notice will a grant recipient be expected to launch their program?
Actual funding access to award recipients is dependent on final budget clearance and adherence to Special Condition requirements. However, award recipients should anticipate begin providing services no later than 90 days after receiving notice.
11. Can agencies that received Fiscal Year (FY) 2010 awards under the Second Chance Act Section 115, also apply for funding again under the FY 2011 solicitation?
There is no regulation that prohibits FY 2010 award recipients from applying again for funding. However, applicants that received FY 2010 awards may not be able to demonstrate the same degree of need as new unfunded applicants.Target Population
12. What is the target population for this program?
The target population should be incarcerated adults and juveniles within a 3-year period before release from a prison, jail, or juvenile facility. The target population for the initiative must be a specific subset of the population of individuals convicted as an adult or adjudicated as a juvenile, and incarcerated in a state, local, or tribal prison; jail or a juvenile detention/correctional facility; juvenile camp; juvenile community-based program; or a juvenile residential facility. For federally recognized Indian tribes, the individuals may be housed in a tribal, state, regional, county, or local jail facility pursuant to state or tribal law.
Applicants must provide justification for selecting the target population and provide supporting documentation for their decision.
13. What is the definition of a “high risk offender”?
There is no official definition contained in the Second Chance Act for “high risk” offenders. However, an applicant should use the definition adopted by their particular jurisdiction. In identifying the target population applicants should be mindful of the requirement to track participants on a quarterly basis.14. Is the applicant agency required to concentrate efforts on offenders returning to a specific geographic community, or can it be a statewide initiative (regardless of the community where the offender is returning)?
Due to the competitive nature of this solicitation the applicant is encouraged to provide as much justification for selecting the target population and providing support documentation for their decision. In addition, applicants need to be aware of the requirements to establish a baseline rate for the target population and the need to track the members of the target population on a quarterly basis.15. May funded programs target specific people who are overrepresented in the criminal justice system?
As a condition for receiving funding, recipients must comply with applicable federal civil rights laws, including Title VI of the Civil Rights Act of 1964. Federal law prohibits a recipient of funding from discriminating in the delivery of services or benefits on the basis of race, color, national origin, sex, religion, or disability. While applicants may design their program to maximize participation by any population overrepresented in the criminal justice system, they may not accept or reject otherwise eligible participants on the basis of their race.
Program-Specific Requirements
16. For the purposes of the solicitation, how is “technology career” defined?
The specific type of technology-based field(s) incorporated into the training program is at the discretion of the applicant. However, the applicant must be able to justify the selected training as technology-related. Some examples of technology-based fields include, but are not limited to, the following:- Computer assisted design in engineering and construction.
- Information technology development and design.
- “Green-technology”-related projects.
- Braille transcription training and certification.
- Wireless and broadband deployment.
- Computer science and programming.
- Other fields as justified by the eligible applicant.
It is not required or mandatory that applicants collaborate with technology industry-related organizations. However, priority consideration will be given to applications that partner with technology industry-related organizations and other entities that can provide resources or expertise to the project. Applicants should demonstrate a high degree of collaboration with workforce employers, and provide documentation demonstrating partnerships, agreements, or memoranda of understanding with relevant employers in the technology areas to which program participants are likely to return.
In addition, priority consideration will be given to applicants that partner with technology industry-related organizations and other entities (including local and small businesses) willing to hire and support high-risk offenders through the learning and job training process.
18. What requirements must technology industry-related organizations meet to qualify as partner agencies?
Technology industry-related organizations and other entities must provide resources or expertise to the project and be willing to hire high-risk offenders.19. Can programs offered to individuals in jails be designed to begin in jail and continue after release due to the shorter lengths of stays?
The solicitation requires that programs must focus on incarcerated adults and juveniles during the 3-year period before release from a prison, jail, or juvenile facility. So programs may be established in a pre-release jail setting if individuals are incarcerated in jail for that length of time.20. Are applicants required to restrict access to any technology tools or resources?
Yes. Applicants must restrict access to the internet by incarcerated persons, as appropriate, to ensure public safety.
21. Can successful applicants provide post-release services to program participants?
Yes. Programs may provide post-release services for a maximum six-month period that provides support for program participants engaged in paths to technology-based careers. However, programs must include a pre-release component during the period of incarceration and cannot be focused solely on post-release services.22. Can successful applicants provide assistance with identifying post-release employment opportunities?
Yes. Award funds may be used to provide job search and placement assistance in the technology field, including stipend support for participants/employers where appropriate. In addition, applicants can also provide career counseling, work-based learning, and other activities as justified by the applicant (where appropriate).Performance Measures
23. What are the performance measures for this program?
The performance measures will require the tracking of key data points. An example would be the Performance Measure, “Percentage of trainees who successfully completed the in-person training program,” which will require the grantee to provide the following data points:
• Number of individuals who completed the training
• Number of individuals who attended each training
A complete list of the Performance Measures can be found on pages 7-9 of the solicitation.
24. What software or tools should grantees use to track performance measures? Are these tools provided by BJA?
Applicants will be required to report their performance measures in BJA’s Performance Measurement Tool (PMT). All applicants selected for an award will subsequently be provided training and additional information on the PMT.
25. How long will grantees need to track client’s performance measure data listed in solicitation? Beyond the funding period?
Recipients may be required to track clients beyond the end of the period for which they receive federal funding. BJA will provide further guidance and assistance to recipients on data collection.
Budget/Allowable Uses
26. What are the allowable uses of funding under this program?
Approved uses for award funds under the technology training program may include the following:- Classroom occupational training.
- Training activities that lead to permanent employment in a technology related field.
- Alignment with apprenticeship programs in the technology field.
- Basic skills training that includes:
- Adult basic education
- English as a Second Language (ESL)
- Job readiness training
- Job search and placement assistance in the technology field.
- Career counseling, work-based learning, and other activities as justified by the applicant (where appropriate).
- Equipment or supplies necessary for participation and completion of the training program.
- Training instructors with technology career experience.
- Post-release services for a maximum 6-month period that provides support for program participants engaged in paths to technology-based careers, including voucher/stipend support.
No.
28. Can grant funds be used to subsidize employers or fund transitional employment programs?
Yes. Award funds may be used for post-release services for a maximum 6-month period that provides support for program participants engaged in paths to technology-based careers, including voucher/stipend support.
29. Does the entire award amount need to be used within the award period?
No. No‐cost extensions will be available to grantees, subject to the approval of BJA. If all award funds are not used (spent) within the award period and completion of the project, the funds will be de-obligated.
30. Are there any limitations on how award funds can be used for employee compensation?
With respect to any award of more than $250,000 made under this solicitation, federal funds may not be used to pay total cash compensation (salary plus bonuses) to any employee of the award recipient at a rate that exceeds 110% of the maximum annual salary payable to a member of the Federal Government’s Senior Executive Service (SES) at an agency with a Certified SES Performance Appraisal System for that year.
A recipient may compensate an employee at a higher rate, provided the amount in excess of this compensation limitation is paid with non-federal funds. The limitation on compensation rates allowable under an award may be waived on an individual basis at the discretion of the Assistant Attorney General (AAG) for the Office of Justice Programs (OJP).
31. Is there a match requirement for this program?
This solicitation does not require a match.
32. Some federal grants require applicants to set aside funds for travel to mandatory grantee meetings. Should mentoring grant applicants budget for any particular training or technical assistance?
Applicants must budget funding to travel to U.S. Department of Justice-sponsored grant meetings. Applicants should estimate the costs of travel and accommodations for three staff to attend two meetings in Washington, D.C.
Collaboration
33. Can a collaboration of entities apply as one applicant?
Yes. However, only one state, unit of local government, territory, or federally recognized Indian tribe, must be designated as the “official” applicant. Priority consideration will be given to applications that demonstrate a high degree of collaboration with workforce employers, and provide documentation demonstrating partnerships, agreements, or memoranda of understanding with relevant employers in the technology areas to which program participants are likely to return.
Technical Application Questions
34. Does the budget narrative count against the 15 page limit?
No.
35. Are there any priority considerations that will be given when evaluating applications for awards?
Priority consideration will be given to applications that:
- Partner with technology industry-related organizations and other entities that can provide resources or expertise to the project. Applicants should demonstrate a high degree of collaboration with workforce employers, and provide documentation demonstrating partnerships, agreements, or memoranda of understanding with relevant employers in the technology areas to which program participants are likely to return.
- Provide training to offenders within 12–18 months prior to release to ensure the training is not obsolete and still current, useable, and transferable.
- Target high-risk offenders for program participation using validated assessment tools. Examples of high-risk offenders may include, but are not limited to: sex offenders, mentally ill offenders, offenders dually diagnosed with major mental health disorders and alcohol or substance addictions at the same time, and other offenders.
- Assess the local demand for employees trained in their targeted field, in the areas to which their program participants are likely to return, to improve the likelihood of post-release employment.
- Partner with technology industry-related organizations and other entities (including local and small businesses) willing to hire and support high-risk offenders through the learning and job training process.
- Provide ongoing training to employers and potential employers on successful approaches to working with trainees/employees engaged through the program.
- Provide individualized education and reentry plans for offenders participating in the training program.
- Leverage existing resources (including current Second Chance programs) to continue the training, job placement, career, and reentry success during the community release phase of reentry.
- Incorporate “peer” mentors when appropriate and include a plan for recruiting, training, and supervising mentors.
All applications will be peer reviewed based on the solicitation requirements. The Directors of BJA and Office of Juvenile Justice and Delinquency Prevention (OJJDP) will then make award recommendations to the AAG for OJP, who will make final determinations.
37. If the state is not applying, can more than one local jurisdiction apply in that state?
Yes, it is possible for several cities, counties, and the state to apply since all are independent jurisdictions.
38. Is there a percentage breakdown for allocation to state versus local government?
No. BJA is cognizant of the need for geographical distribution as well as some level of equity among states, locals, and tribes.
39. How will submissions from multiple jurisdictions in the same state be viewed? How would it reflect on a state if multiple agencies applied from that state?
Submissions from multiple jurisdictions in the same state will be viewed on the individual merit of each application that meets the solicitation requirements.
Other
41. Will there be future opportunities to apply for funding under this program?
All future BJA funding opportunities will be based on Congressional approved appropriations.
42. Can grant funds be used to enhance existing reentry programs, or are funds limited to new programs?
Federal funds cannot be used to supplant existing services. Federal funds provided under the Second Chance Act are meant to be one of the sources of program funding. They may not to be used to replace other funding sources.
43. Is there someone specific to contact with questions about the process or program?
For technical assistance with submitting the application, contact the Grants.gov Customer Support Hotline at 800–518–4726 or via e-mail to support@grants.gov. The Grants.gov Support Hotline hours of operation are 24 hours, 7 days a week, except federal holidays.
For assistance with any other requirement of this solicitation, contact the BJA Justice Information Center at 1–877–927–5657. The BJA Justice Information Center hours of operation are 8:30 a.m. to 5:00 p.m. eastern time, Monday through Friday, and 8:30 a.m. to 8:00 p.m. eastern time on the solicitation close date.
Sunday, February 13, 2011
Critical Digital Literacy: Use in Crime
Digital literacy can prevent individuals from believing hoaxes that are spread Online or are the result of photo manipulation. E-mail frauds and phishing often taking advantage of the digitally illiterate, costing victims’ money and making them vulnerable to identity theft.
For less than $15.00, you can purchase any of the following books and prevent losing over $1,500 due to identity theft schemes.
Thursday, February 10, 2011
President Obama, the Supreme Court and the 14th and 15th Amendments
According to the reviews, this is a must-read book to understand the deep background of the Civil Rights movement of the 1950s and 1960s that allowed the Supreme Court to essentially abrogate the protection of the 14th and 15th Amendments as they applied to African Americans. This meant that discrimination against freedmen and their descendents was essentially thrown back into the hands of land-owning southerners. President Obama as a former attorney could leverage these historical accounts to prevent similiar circumstances from continuing to occur in digital communication networks where African Americans are not given fair opportunities to be network owners.
Also on the journey to Digital Equality, society must consider digital media education. The reviewers state this is the most thorough book you will read on Brown v. Board of Education. The author writes based on his experience as a lawyer, a historian and a journalist who witnesses a multitude of events which he depicts.
In some respects, this book could inform President Obama and his team on how the Supreme Court and its process of decision-making positively and negatively impacts Education Equity and Digital Equality.
Purchase and share your views.
Also on the journey to Digital Equality, society must consider digital media education. The reviewers state this is the most thorough book you will read on Brown v. Board of Education. The author writes based on his experience as a lawyer, a historian and a journalist who witnesses a multitude of events which he depicts.
In some respects, this book could inform President Obama and his team on how the Supreme Court and its process of decision-making positively and negatively impacts Education Equity and Digital Equality.
Purchase and share your views.
Tuesday, February 8, 2011
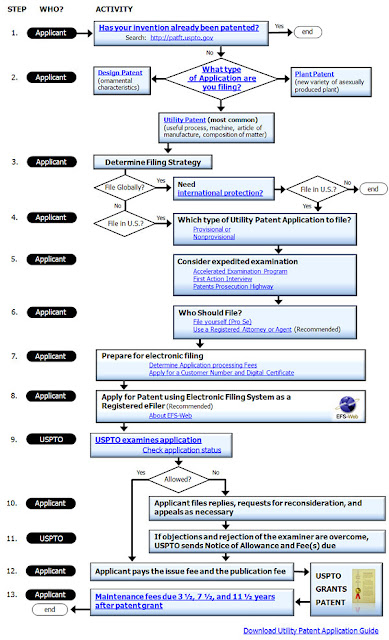
Electronically Filing a Patent requires critical digital literacy
When we got to the Step 5 section of the diagram the site started challenging the Fonts embedded in our PDF document. A few top content management staff was summons to address the following error messages and get the patent filed. After the event, one neophtype asked whether this was a good example of critical digital literacy. The other members smiled as to imply Absolutely!
The attached PDF file references a non-embedded font: ArialMT. Please remove file, embed the font and reattach.
The attached PDF file references a non-embedded font: TimesNewRomanPS-BoldMT. Please remove file, embed the font and reattach.
The attached PDF file references a non-embedded font: TimesNewRomanPS-ItalicMT. Please remove file, embed the font and reattach.
The attached PDF file references a non-embedded font: Verdana. Please remove file, embed the font and reattach.
The attached PDF file references a non-embedded font: Verdana-Bold. Please remove file, embed the font and reattach.
The attached PDF file references a non-embedded font: TimesNewRomanPS-BoldItalicMT. Please remove file, embed the font and reattach.
The attached PDF file references a non-embedded font: ArialMT. Please remove file, embed the font and reattach.
The attached PDF file references a non-embedded font: TimesNewRomanPS-BoldMT. Please remove file, embed the font and reattach.
The attached PDF file references a non-embedded font: TimesNewRomanPS-ItalicMT. Please remove file, embed the font and reattach.
The attached PDF file references a non-embedded font: Verdana. Please remove file, embed the font and reattach.
The attached PDF file references a non-embedded font: Verdana-Bold. Please remove file, embed the font and reattach.
The attached PDF file references a non-embedded font: TimesNewRomanPS-BoldItalicMT. Please remove file, embed the font and reattach.
Saturday, February 5, 2011
Saying goodbye to public schools and “just-in-case learning”
Is technology opening up a “golden age” of learning for everyone? Allan Collins and Richard Halverson argue, without placing any bets, that it might. Adult education and learning centers are growing, distance education through the Internet is more available, and companies are issuing their own technical certificates, among other developments.
The key question is how to improve education outside of schools, since that’s where most of the learning will take place. Collins and Halverson argue this shift is inevitable. Schools – which foster “just-in-case learning” – are outmoded compared to technology, which fosters “just-in-time learning.”
In the real world specialization is replacing standardized assessments, customization is more important than uniform learning, diverse knowledge sources are more important than expert teachers, learning by doing is more important than learning by acquisition, and reliance on outside sources is more important than knowledge in the head.
But visionaries are need to make sure values such as equity and diversity continue to be pursued outside of public education – pursuits, I would argue, that never really came close to succeeding. Can the new golden age do any worse?
Read the full article, RETHINKING EDUCATION IN THE AGE OF TECHNOLOGY:
THE DIGITAL REVOLUTION AND THE SCHOOLS.
URL: http://ocw.mit.edu/courses/media-arts-and-sciences/mas-714j-technologies-for-creative-learning-fall-2009/readings/MITMAS_714JF09_read03_coll.pdf
The key question is how to improve education outside of schools, since that’s where most of the learning will take place. Collins and Halverson argue this shift is inevitable. Schools – which foster “just-in-case learning” – are outmoded compared to technology, which fosters “just-in-time learning.”
In the real world specialization is replacing standardized assessments, customization is more important than uniform learning, diverse knowledge sources are more important than expert teachers, learning by doing is more important than learning by acquisition, and reliance on outside sources is more important than knowledge in the head.
But visionaries are need to make sure values such as equity and diversity continue to be pursued outside of public education – pursuits, I would argue, that never really came close to succeeding. Can the new golden age do any worse?
Read the full article, RETHINKING EDUCATION IN THE AGE OF TECHNOLOGY:
THE DIGITAL REVOLUTION AND THE SCHOOLS.
URL: http://ocw.mit.edu/courses/media-arts-and-sciences/mas-714j-technologies-for-creative-learning-fall-2009/readings/MITMAS_714JF09_read03_coll.pdf
Friday Night DML E3D Session - extract
February 04, 2011 - DML E3D Level P session
Do you need a good tracker that you can use to track your partners and see where they go?
To the male facilitator's surprise none of the 5 females wanted to track their male partners. The other males in the session seemed equally surprised. The group discussed some of the options when it comes to accomplishing this, as well as some of the alleged bonuses: you can see much more than where the person is. In fact, with today's digital technologies, you will see where the person is in real-time based on the GPS data, as well as text messages being sent and received. You can also see emails, browser history, phone contact information and call logs - if they are carrying a smartphone (i.e. iPhone).
The participants' questions for our readers are listed below. We would appreciate your responses:
Would you approve of being tracked?
Would you purchase a tracker for your partner?
Would you feel less trusted if you partner requested that you be tracked?
Would you be interested in a method to disable the tracker?
Would you consider wedding rings a form of tracking?
Do you need a good tracker that you can use to track your partners and see where they go?
To the male facilitator's surprise none of the 5 females wanted to track their male partners. The other males in the session seemed equally surprised. The group discussed some of the options when it comes to accomplishing this, as well as some of the alleged bonuses: you can see much more than where the person is. In fact, with today's digital technologies, you will see where the person is in real-time based on the GPS data, as well as text messages being sent and received. You can also see emails, browser history, phone contact information and call logs - if they are carrying a smartphone (i.e. iPhone).
The participants' questions for our readers are listed below. We would appreciate your responses:
Would you approve of being tracked?
Would you purchase a tracker for your partner?
Would you feel less trusted if you partner requested that you be tracked?
Would you be interested in a method to disable the tracker?
Would you consider wedding rings a form of tracking?
Thursday, February 3, 2011
Looking for work... a job? Improve your chances with Critical Digital Literacy.
Without digital literacy experience, a person attempting to use any of the following strings of text in a Google search could become discouraged, discontented and disappointed faster than it would take a million results to be returned.
"Looking for a job"
About 4,130,000 results (0.16 seconds) - major results from job search, advertisement, and referral sites
"Looking for work"
About 2,870,000 results (0.13 seconds) - major results from individuals, recruiters, advertisers
"Found a job"
About 2,460,000 results (0.20 seconds)
- Ironically most results relate to Talking Head lyrics
The following sources would provide some direction for getting
started but your best options is to enroll in a DML E3D oriented program
- contact dml.e3d@gmail.com for sources.
"Looking for a job"
About 4,130,000 results
- Ironically most results relate to Talking Head lyrics
The following sources would provide some direction for getting
started but your best options is to enroll in a DML E3D oriented program
- contact dml.e3d@gmail.com for sources.
Wednesday, February 2, 2011
Digital Records vs Antiquated paper record-keeping

Who: Arlington National Cemetery, Booz Allen Hamilton, Science Applications International Corp. and Mitre
What: Antiquated paper record-keeping and lack of oversight
When: Over a ten month period
Where: Arlington, Virginia
Why: Greed, Digital Inequity, ...
Washington Post full story...
Do it yourself sources;
Discovering the Digital Record -- The Questions for Examination
The Digital Records Conversion Process: Program Planning, Requirements, Procedures
Selecting Storage Media for Long-Term Access to Digital Records.: An article from: Information Management Journal
Subscribe to:
Posts (Atom)